Cryptography is the foundation of digital security—from protecting your messages and passwords to securing online payments and cloud data. At the core of cryptographic systems are two main types of encryption: symmetric and asymmetric.
In this article, I’ll walk through how each method works, explore their strengths and limitations, and explain why modern security often relies on a combination of both.
Symmetric Cryptography
In symmetric cryptography, a single secret key is used for both encryption and decryption. This means the key must be kept secure and never shared with unauthorized parties.
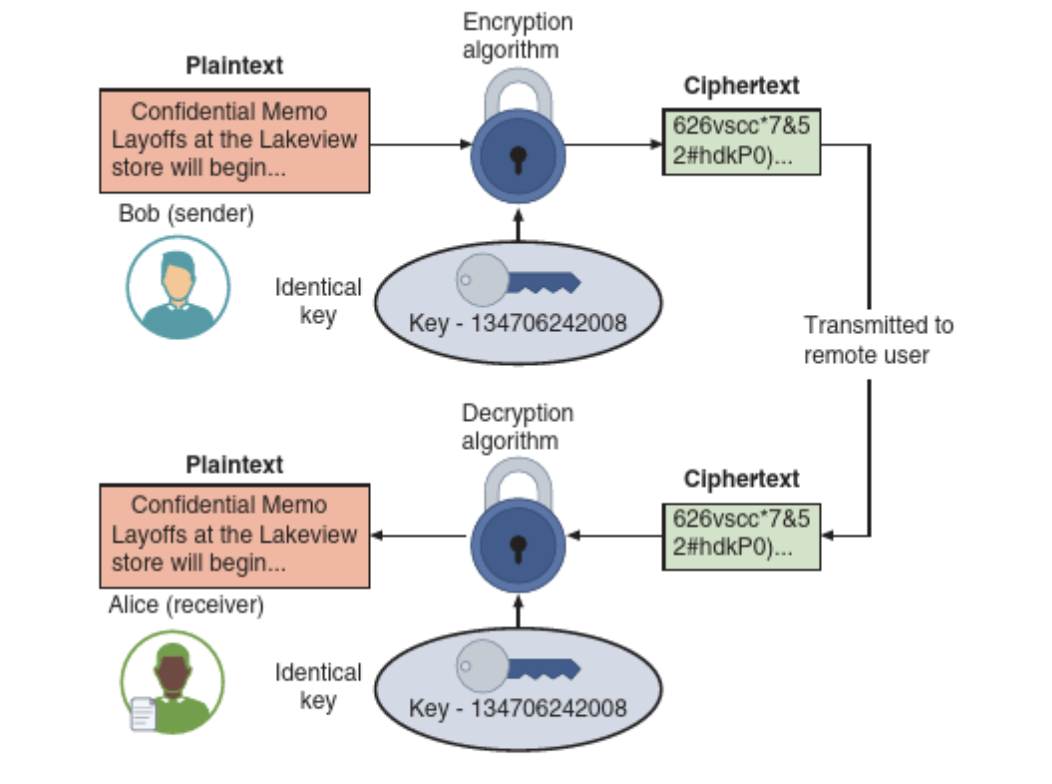
Symmetric cryptography. (Image source: Ciampa, M. (2024). Comptia+ security+ guide to network fundamentals. Cengage.)
However, this raises a challenge: how to safely transfer the secret key between trusted parties. Symmetric methods alone do not provide a secure channel for key exchange.
Asymmetric Cryptography
In asymmetric cryptography, a public key is used to encrypt the message and a corresponding private key is used to decrypt it. The keys can also be used in reverse, depending on the use case.
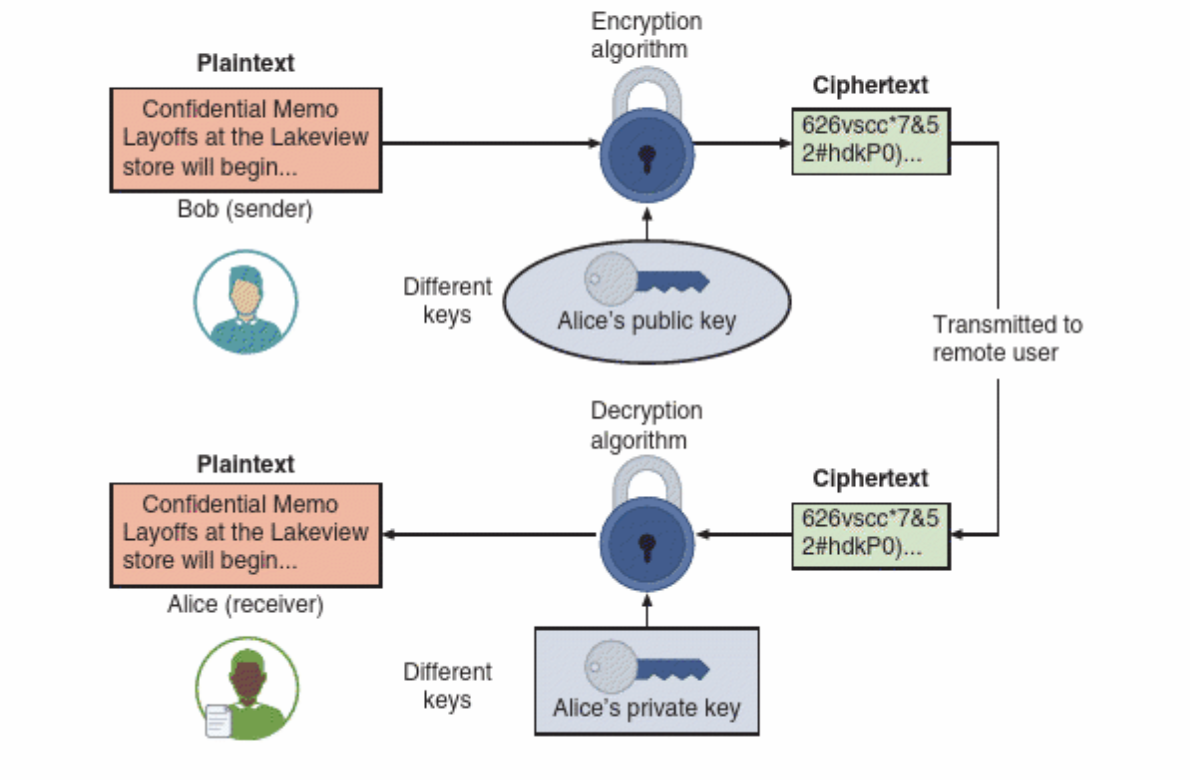
Asymmetric cryptography. (Image source: Ciampa, M. (2024). Comptia+ security+ guide to network fundamentals. Cengage.)
Case Studies
Case 1: Ensuring Information Confidentiality
While symmetric methods can achieve strong encryption with relatively small key sizes, they lack a secure method to exchange the secret key. This is where asymmetric cryptography comes in: it allows safe transmission of the secret key.
However, asymmetric encryption is computationally more intensive and slower than symmetric methods. In practice, a hybrid approach is commonly used:
- The message is encrypted using a symmetric algorithm (e.g. AES) for performance.
- The symmetric key is encrypted using an asymmetric algorithm (e.g. RSA) for secure transmission.
This method offers both high security and good performance.
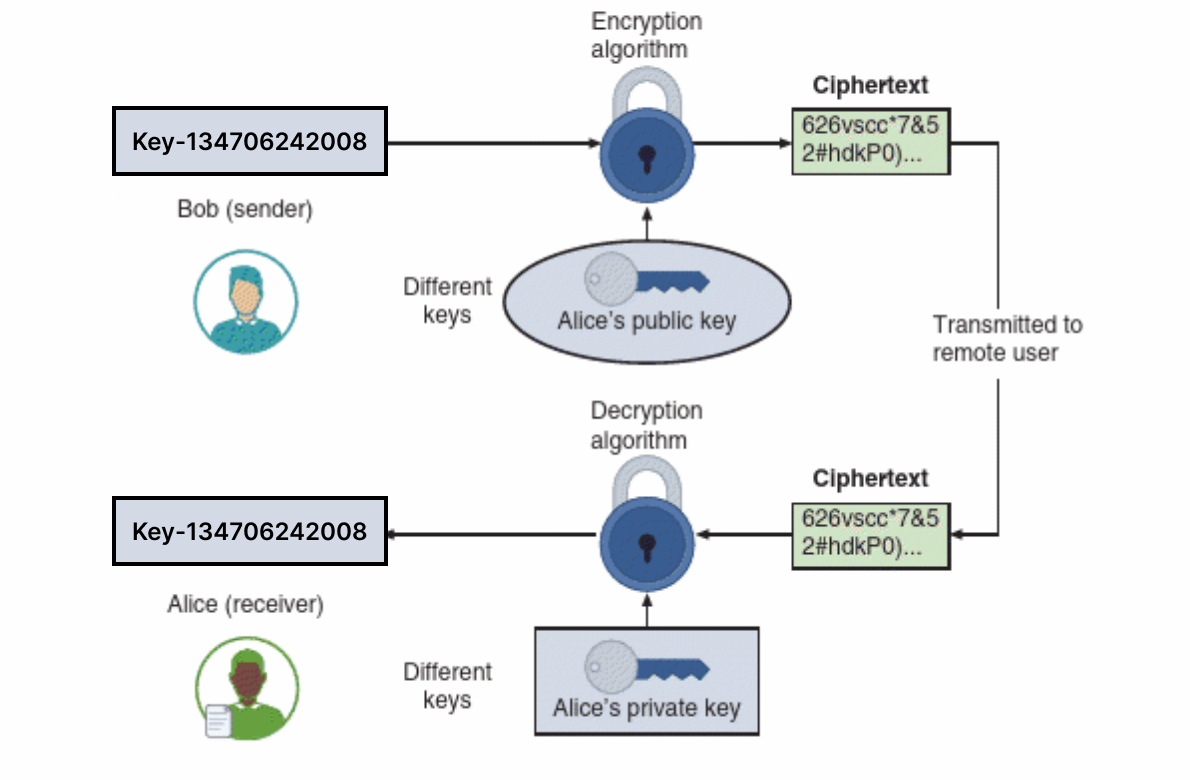
Sharing the secret key using asymmetric cryptography (Image adapted from source: Ciampa, M. (2024). Comptia+ security+ guide to network fundamentals. Cengage.)
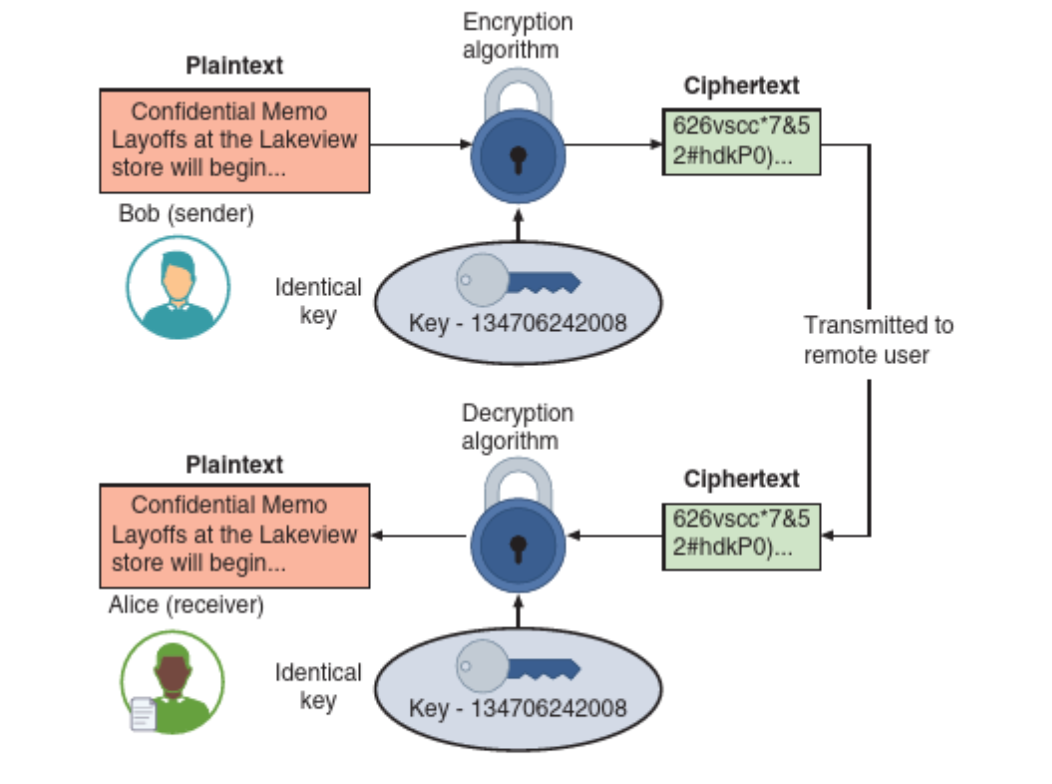
Sharing the message using symmetric cryptography (Image source: Ciampa, M. (2024). Comptia+ security+ guide to network fundamentals. Cengage.)
Case 2: Proving Authenticity
Authenticity means confirming that a message was indeed sent by the claimed sender and has not been tampered with. To ensure this, digital signatures are used.
A digital signature is created by hashing the message to produce a digest and then encrypting the digest with the sender's private key. The receiver:
- Decrypts the signature using the sender's public key.
- Hashes the received message and compares it with the decrypted digest.
If they match, this confirms:
- The message was sent by the legitimate sender (authenticity).
- The message was not altered in transit (integrity).
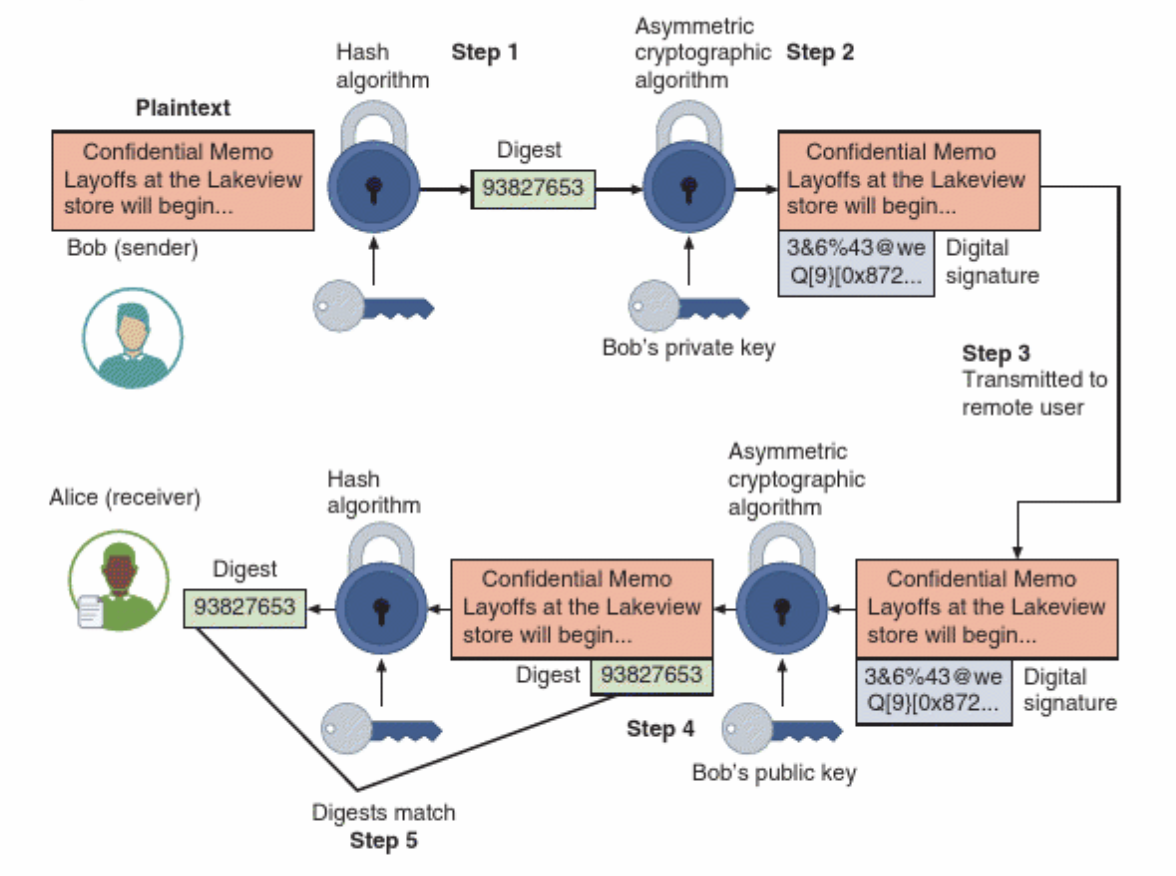
Digital signature. (Image source: Ciampa, M. (2024). Comptia+ security+ guide to network fundamentals. Cengage.)
It must be noted, however, that digital signatures do not ensure confidentiality. The message is still sent in plain text alongside its signed digest. Anyone can read the message — the signature only verifies authenticity and integrity.
To ensure confidentiality in addition to authenticity, the signed message must also be encrypted using symmetric or asymmetric encryption, as described in Case 1.
Conclusion
Symmetric and asymmetric cryptographic algorithms differ in key management, computational performance, and application:
- Symmetric: fast, simple, but hard to share keys securely.
- Asymmetric: secure key exchange and digital signatures, but slower.
Each method provides different security properties—such as confidentiality, integrity and non-repudiation. In real-world systems, these approaches are often combined to create secure, performant communication protocols. The key is to choose the right tools based on the security goals and context of your project.